Containerisation has revolutionised software development and deployment, providing unparalleled versatility and scalability. Still, this change in perspective also brings unique security challenges.
This comprehensive analysis will thoroughly examine container security from all perspectives, providing the necessary understanding to protect your containerised environments.
Containerisation: A Fundamental Shift in Application Delivery
Containerization is a form of operating system virtualization that packages an application and its dependencies into a self-contained, isolated unit called a container.
Unlike traditional virtualization, which involves running multiple virtual machines on a single host, containerization allows multiple containers to share the host operating system kernel, ensuring efficient resource utilization and rapid application deployment. This technique offers a variety of benefits:
Lightweight: Containers use the host’s kernel, resulting in greater resource efficiency than typical virtual machines.
Portability: Containers provide uniform execution across various environments, making development, testing, and deployment easier.
Scalability: Applications may be easily expanded or reduced by adding or deleting containers, allowing them to adjust to different workloads.
“Containerisation has had a significant influence by enabling shorter release cycles, efficient processes, and cost optimisation”.
Some prominent container technologies:
– Docker: An industry leader in the field of containerisation, offering a user-friendly interface and a wide range of tools and resources.
– Kubernetes: An advanced management system specifically created to efficiently handle extensive container deployments, automate the process of scaling, and ensure consistent availability.
– Podman: A container engine that doesn’t require a daemon. It provides Docker-compatible features and is particularly attractive to users looking for a more lightweight solution.
– Containerd: A high-performance container runtime that acts as the fundamental technology for Docker and Kubernetes.
Although Docker continues to be the preferred choice, Kubernetes is quickly gaining popularity, especially in commercial settings where complex, distributed applications are common.
Foundations of Container Security: Techniques for Isolation
Isolation is the primary foundation of security in containerised settings. It involves three primary strategies:
– Resource isolation: Ensures that each container is allocated specific constraints on CPU, memory, and storage use, so preventing one container from depriving another of resources. Linux control groups (cgroups) may be used to do this.
– Kernel-Level Isolation: Containers, although sharing the host kernel, use methods like namespaces to provide separate contexts for processes. This guarantees that the processes of one container cannot disrupt or affect the operations of another container.
– Network isolation: Refers to the practice of assigning distinct IP addresses and network interfaces to containers, which restricts their ability to communicate with one other across a network.
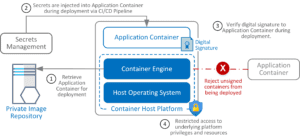
Virtual Machines VS. Containers
Like containers, virtual machines are also prominent technologies that have emerged with advancements in virtualization. But how are they different and/or similar?
Virtual machines (VMs) emulate an entire operating system, providing complete isolation but consuming significant resources. Containers, on the other hand, share the host’s kernel, offering lightweight isolation and faster startup times.
VMs are best suited for running multiple OS environments, while containers excel at packaging and deploying applications consistently across different platforms. However, containers may have potential security risks due to shared kernel space.
Ultimately, the choice between VMs and containers depends on specific requirements such as compatibility, isolation level, and resource efficiency.
Implementing Vulnerability Management: A Proactive Strategy for Enhancing Security
Containers, like other software, are prone to vulnerabilities. An effective vulnerability management plan is crucial:
– Implement Patch Management: Timely apply security fixes to both container images and the host operating system.
– Implement runtime protection: Deploy security solutions that actively monitor the behavior of containers in real time. These solutions are designed to identify any abnormal activities and prevent any harmful actions from occurring.
– Ensuring the safety and reliability of the supply chain: Ensure the accuracy and authenticity of container images to prevent the infiltration of hacked or malicious code.
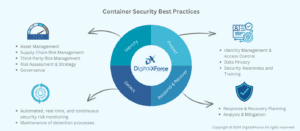
Optimal Methods for Ensuring the Security of Containers
Adhering to optimal methods is essential for establishing a safe containerized environment.
– Least Privilege: Execute containers with the minimal required rights, avoiding execution as the root user wherever feasible.
– Image Hardening: Use of minimum base images and the elimination of extraneous packages to decrease the vulnerability of the system to attacks.
– Secrets Management: Safeguard confidential data like passwords and API keys by storing them in specialized secrets management systems instead of including them directly into container images.
– Network segmentation: Dividing your container network into smaller pieces to restrict the possible impact of a breach.
– Periodic inspections: Perform regular security audits to evaluate the security posture of your container environment and detect areas that need improvement.
– Utilise Container Security Systems: Provide extensive protection, such as vulnerability screening, runtime defense, and compliance monitoring.
Advanced security considerations
For organizations with strict security needs, it is advisable to consider the following:
– Implement kernel-level security modules: Such as AppArmor or SELinux to impose more stringent access restrictions and restrict container processes.
– Build Trust: Implement a zero-trust security framework, in which trust is never presumed and each request is authenticated, to enable digital trust.
– Implement security measures via the use of code: Security rules are defined as code and then integrated into infrastructure as code (IaC) procedures to ensure consistent enforcement.
The Future of Container Security
Container security is a continuous process, rather than a final goal. As the container environment undergoes constant changes, it is essential to adapt and enhance your security measures accordingly. To maintain the security and resilience of your containerized environments, it is important to keep updated on the newest threats and implement a proactive and layered security strategy.

About The Author
Tataksh Bhagat is a cybersecurity engineer at iTRUSTXForce. While his passion for cybersecurity, the thrill of solving complex problems, and a commitment to protecting digital information against emerging threats, brought him into this field, he is currently pursuing a B.E. in Computer Engineering, at Thapar Institute of Engineering and Technology, with certifications in Network Essentials from Cisco Academy and Cyber Security Essentials from Thapar University.