
In today’s interconnected business landscape, organizations increasingly rely on third-party vendors, suppliers, and service providers to streamline operations, access specialized expertise, and drive innovation.
However, this dependency also introduces significant risks, ranging from data breaches and cyber threats to operational disruptions and regulatory non-compliance. As a result, effective third-party risk management (TPRM) has become imperative for organizations across industries.
The Current State of TPRM and the Need for a Trust-Focused Approach
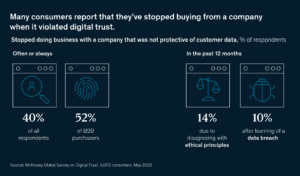
According to a 2023 report by Deloitte, 83% of organizations experienced a third-party incident in the past three years, with the average cost of such incidents exceeding $10 million. Furthermore, the Ponemon Ponemon Institute’s “Data Risk in the Third-Party Ecosystem” study revealed that 49% of organizations experienced a data breach caused by third-party vendors or suppliers.
These alarming statistics underscore the need for a comprehensive and trust-focused TPRM strategy. Traditional approaches to TPRM often fall short, failing to adequately address the complexities of today’s digital ecosystem and the evolving threat landscape. A trust-enabled TPRM strategy recognizes the pivotal role of digital trust in mitigating risks associated with third-party relationships.
Digital trust encompasses various elements, including cybersecurity, data privacy, and the integrity of digital infrastructure. By fostering digital trust throughout the third-party ecosystem, organizations can proactively identify and mitigate potential risks, ensuring the confidentiality, integrity, and availability of sensitive data and systems.
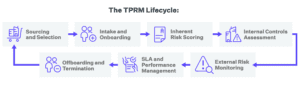
Implementing a Trust-Focused Strategy for TPRM
Developing and implementing a trust-focused TPRM strategy requires a holistic and systematic approach. Here are key steps organizations should consider:
- Establish a robust governance framework: Implement a well-defined governance structure with clear roles, responsibilities, and decision-making processes for TPRM. This framework should encompass all stages of the third-party lifecycle, from vendor selection and onboarding to ongoing monitoring and offboarding.
- Conduct comprehensive risk assessments: Perform thorough risk assessments to identify and prioritize potential risks associated with each third-party relationship. This assessment should consider factors such as the services provided, the sensitivity of the data involved, and the potential impact on the organization’s operations and reputation.
- Implement robust security controls: Based on the risk assessments, implement appropriate security controls and measures to mitigate identified risks. These controls may include access management, data encryption, secure communication protocols, and regular security audits and penetration testing.
- Foster transparency and collaboration: Establish open lines of communication and collaboration with third-party vendors, encouraging transparency and ensuring alignment on security and privacy practices. Regular meetings, joint incident response planning, and shared performance metrics can help foster trust and accountability.
- Continuous monitoring and oversight: Implement continuous monitoring processes to track and assess third-party performance, compliance, and potential risks. This may involve periodic audits, security assessments, and real-time monitoring of critical systems and data flows.
Top 5 Best Practices for Trust-enabled TPRM
- Develop a comprehensive third-party risk management framework: Establish a robust TPRM framework encompassing all stages of the third-party lifecycle, from vendor selection and due diligence to ongoing monitoring and termination. This framework should align with industry standards and best practices, such as the NIST Cybersecurity Framework and the ISO 27001 standard for information security management.
- Prioritize cybersecurity and data privacy: Ensure that third-party vendors and suppliers adhere to stringent cybersecurity and data privacy standards. Conduct thorough assessments of their security posture, including their ability to protect sensitive data, detect and respond to cyber threats, and comply with relevant regulations (e.g., GDPR, CCPA).
- Implement robust access controls and monitoring: Implement strict access controls and monitoring mechanisms to govern third-party access to your organization’s systems and data. This may include multi-factor authentication, least privilege access principles, and continuous monitoring of user activities and data flows.
- Foster transparency and accountability: Establish clear contractual agreements and service-level agreements (SLAs) with third-party vendors, outlining their responsibilities, performance metrics, and accountability measures. Regular audits, incident reporting, and open communication channels can help build trust and ensure compliance.
- Leverage advanced technologies: Advanced technologies, such as DigitalXForce offer outcome-based integrated risk management, AI-powered security blueprint generator, and cyber insurance application processor. Our Suite of automated monitoring and reporting tools covers board-level risk analytics, risk remediation planning, policy review, and security management and operations plan generation to streamline TPRM processes, enhance risk visibility, provide a security posture blueprint, and enable proactive risk mitigation.
Conclusion
Building trust and managing risks associated with third-party relationships is imperative in the digital age. Organizations must adopt a comprehensive strategy focused on digital trust and adhere to best practices for trust-enabled third-party risk management to safeguard their operations, protect sensitive data, and maintain a strong security posture.
 "Digital trust" cybersecurity solutions enabling automated, real-time risk mitigation are crucial for protecting organizations in today's threat landscape.
"Digital trust" cybersecurity solutions enabling automated, real-time risk mitigation are crucial for protecting organizations in today's threat landscape.