
In today’s globalized economy, organizations rely heavily on third-party vendors, suppliers, and partners for key business operations. This interconnectedness exposes organizations to the risks that their third parties carry, potentially disrupting operations or compromising data. \
Third-Party Risk Management (TPRM) has transitioned from a compliance-driven checkbox exercise to a comprehensive and dynamic risk assessment practice.
Increasing cybersecurity threats, regulatory scrutiny, supply chain complexities, and the need for operational resilience drive this evolution. Organizations that effectively adapt to these changes are better equipped to manage third-party risks, ensure compliance, and build a more resilient business ecosystem.
Over the past few years, breaches due to third-party vulnerabilities have become a significant concern, with the Ponemon Institute’s 2022 Cost of a Data Breach Report revealing that 19% of data breaches involve third-party vendors, costing an average of $4.33 million per breach.
In a 2021 survey by Opus and Ponemon, 51% of organizations reported experiencing a data breach caused by a third party, while third-party breaches increased by 35% between 2019 and 2020. See: Security Magazine
Supply chain attacks have surged by 78%, exemplified by the SolarWinds attack that affected 18,000 customers globally. Meanwhile, a 2022 Netwrix survey indicates that 55% of organizations consider third-party cloud services the leading source of security risks.
Despite these risks, only 34% of organizations keep an accurate inventory of third parties with whom they share sensitive data, emphasizing the need for stronger third-party risk management practices.
Elements of Third-Party Risk Management
There has been a massive shift from Self-Assessment questionnaires to TPRM leveraging external risk intelligence, continuous monitoring services, and artificial intelligence to gain actionable risk insights.
– Who is assessed as a Third-party? These include Business Providers, Suppliers, Support Providers, Managed Services Providers, Brokers, Cloud Service Providers, and Supply Chain providers like Software vendors and Hardware OEMs.
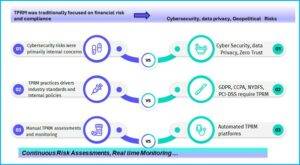
– Risks associated with Third parties are Cyber Security Risks, Reputational Risks, Financial Risks, Regulatory Compliance Risks, Strategic Risks, Legal Risks, Geopolitical risks, and Vendor Lock-in or Lock-out Risks.
– Challenges faced by organizations today are the lack of continuous monitoring and assessment of the Third-Party environments that can give real-time risk posture and actionable data with insights to treat the Risks.
There is a significant cost impact due to breaches or managing Third-Party Risk Assessments which typically results in a lot of administrative Overhead and loss of Productivity.
– Due to a mix of Manual and semi-automated, point-in-time Audits, Data Accuracy is not that high.
– Lack of Visibility of relative standing compared to Industry Peers.
Organizations must now have a robust TPRM Program in place. Key Foundational components of TPRM are shown in the figure below:
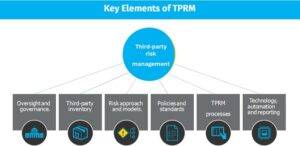
TPRM program may have varying levels of maturity and an assessment should be carried out to arrive at the current Maturity level. Subsequently, with the new era of tools, automation, and AI, a comprehensive upgrade for the three pillars, People, Process and Technology may be planned based on Cost vs Benefit.
Here, a view needs to be taken whether risks outweigh the cost of doing business. This would require continuous ongoing Risk Assessment. In the figure below, the maturity levels are shown:
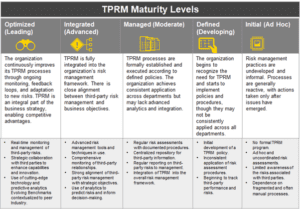
This progression ensures that an organization can not only protect itself from the potential negative impacts of third-party relationships but also leverage these relationships for strategic advantage.
DigitalXForce: Streamlining TPRM with Cutting-Edge Precision
DigitalXForce uniquely addresses these challenges. Real-time data is collected continuously and analyzed following the NIST CSF and frameworks, regulatory frameworks. The key highlights of the solution are:
- Real-time Risk Assessment through continuous monitoring
- Dynamic Risk adjustment based on business objectives.
- Continuous attack surface identification and detection of vulnerabilities
- Nimble-footed and quick to evolve as the digital landscape of industry changes.
- Past data compared with current while assessing security posture.
- AI-powered analysis of contracts, policies, and assessment data to give a real-time compliance view.
- Relative performance concerning industry peers helps organizations gain a competitive edge.
- Battery of Experts advising the Clients on Cyber Security Strategy
- Ingests Data from various leading OEM Security tools and Enterprise platforms.
Disruption with proprietary developed tools and risk assessment algorithms, a constantly evolving database, and AI-powered data analysis, DigitalXforce is way ahead of its market peers.
DigitalXforce defines TPRM via its approach that entails, considering Inherent Risks that would be contextualized to the organization assessed and considering the industry benchmarks.
Organizations going for a Third-Party Risk Assessment would get to see Centralized Dashboards and Reports as below:

Conclusion
Organizations strive to move from lower to higher maturity levels to enhance their resilience against third-party risks. Progressing through these levels involves increasing sophistication in processes, wider integration across the enterprise, and a shift from tactical, reactive measures to Strategic, Proactive Management.
About The Author

Akshay Kant is an IT and Cyber Security veteran at iTrustXForce with over 25 years of experience. His expertise includes Cyber Security, Cloud Security, ISO 27001 Lead Auditing, Data Privacy and Protection Compliance, and Risk Advisory. Akshay is skilled in pre-sales, training, and project management.



