
The Secure Software Development Life Cycle (SSDLC) is a comprehensive framework designed to integrate security practices into each phase of software development. By embedding security considerations from the outset, organizations can create software resilient to attacks and capable of safeguarding sensitive information.
This article provides an overview of the SSDLC, highlights its importance, and outlines best practices for embedding security into each phase of the software development process.
Why Secure Software Development Life Cycle Matters?
Software security is paramount in the era of rapid digital transformation. Software applications are central to business operations and often handle vast amounts of sensitive data. If not developed with security in mind, these applications can become prime targets for cyberattacks, potentially leading to data breaches, financial losses, and reputational damage.
The SSDLC helps organizations mitigate these risks by ensuring that security is a key consideration throughout the development lifecycle.
Embedding Security Trust into All Phases of the Secure SDLC
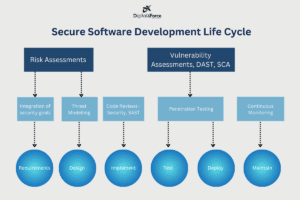
The Secure SDLC approach emphasizes integrating security measures throughout every stage of development, from initial planning to deployment and maintenance. Here’s how to embed security trust into all phases of the software development life cycle:
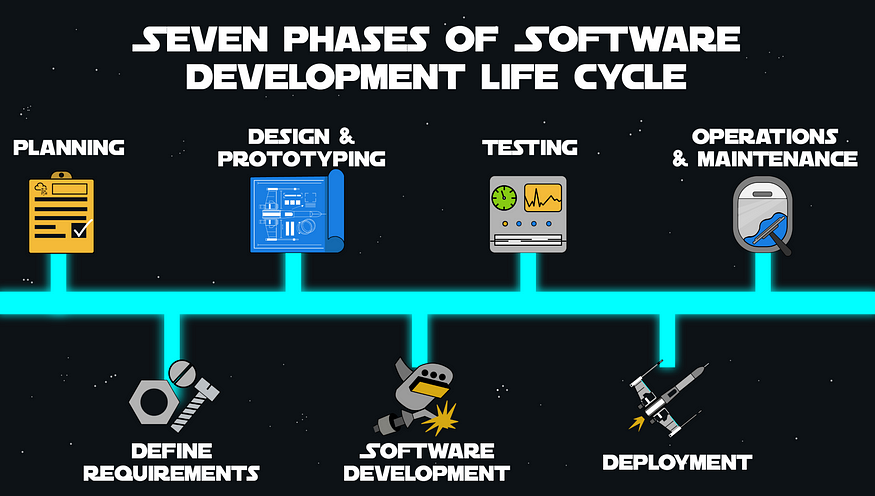
Planning
Security Requirements: Identify and incorporate security requirements into the project plan. Conduct a risk assessment to pinpoint potential threats and vulnerabilities and determine appropriate controls.
Risk Assessment: Evaluate potential security threats and define mitigation strategies early in the planning phase.
Requirements and Analysis
Clear Security Requirements: Define security requirements clearly and ensure they are understood and integrated into the software design.
Threat Modeling: Develop a threat model to identify potential attacks and outline defensive measures.
Design and Prototyping
Secure Design Patterns: Utilize secure design patterns and conduct security reviews of the design.
Security Controls: Implement appropriate security controls during the design phase to mitigate identified threats.
Development
Secure Coding Practices: Adhere to secure coding standards and use static analysis tools to identify vulnerabilities.
Code Reviews: Conduct regular code reviews to ensure adherence to security practices.
Testing
Security Testing: Perform rigorous security testing, including penetration testing and vulnerability assessments, to identify and address potential security flaws.
Automated Testing Tools: Utilize automated testing tools to streamline security testing processes.
Deployment
Secure Deployment Practices: Follow best practices for secure deployment, including security assessments of the deployment environment.
Access Controls: Implement robust access controls and other security measures during deployment.
Maintenance
Regular Patching: Continuously patch the software to address new vulnerabilities.
Ongoing Monitoring: Monitor the software for security issues and conduct regular security reviews to maintain security over time.
By embedding security considerations into each phase, organizations can proactively identify and address potential vulnerabilities, reducing risks and enhancing the overall integrity of their software products.
Best Practices to Secure the SDLC
Securing the Software Development Life Cycle (SDLC) is essential for creating robust, reliable, and protected applications. Consider the following best practices:
Prepare Your Organization
Security Policies: Establish a clear secure software development policy outlining security expectations and requirements.
Training and Resources: Provide training on secure coding practices, threat modeling, and other relevant topics.
Secure Development Environment: Implement controls to secure the development environment, such as access controls and vulnerability management.
Change Management: Implement a secure change management process to review and approve all changes.
Add Security Practices to Organizational Processes
Threat Modeling: Conduct threat modeling during the design phase to identify and mitigate potential attacks.
Secure Design Patterns: Use secure design patterns to build resilience against common attacks.
Secure Coding Practices: Follow secure coding practices and conduct regular code reviews.
Regular Assessments: Perform regular security assessments and reviews to ensure ongoing security.
Proactively Assess and Verify Security
Security Assessments: Conduct security assessments of the deployment environment to identify and mitigate potential vulnerabilities.
Patch Management: Regularly patch the software to fix known vulnerabilities.
Monitoring: Continuously monitor the software for unusual activity or potential security issues.
Regular Security Reviews: Conduct periodic security reviews of the software’s architecture, design, and implementation.
Respond to Vulnerabilities
Vulnerability Identification: Establish processes for identifying vulnerabilities through static analysis tools and code reviews.
Impact Assessment: Assess the potential impact of identified vulnerabilities to determine the appropriate response.
Prioritize Responses: Prioritize addressing vulnerabilities based on their potential impact.
Communication: Communicate with stakeholders about vulnerabilities and the actions being taken to address them.
Conclusion
The Secure Software Development Life Cycle (SSDLC) is crucial for developing secure software that can withstand cyber threats and protect sensitive data. By embedding security practices into each phase of the software development process, organizations can proactively identify and mitigate potential vulnerabilities.
This not only enhances the security of the final product but also helps organizations comply with industry regulations and build a reputation for developing secure software. Adopting the SSDLC framework ensures that security is fundamental to software development, leading to more robust and resilient applications.

About The Author
Shivam is a Cybersecurity Engineer at iTrustXForce with expertise in C/C++ and Python. He has a solid foundation in computer fundamentals and cybersecurity, specializing in OT and Application Security.



